Operational Technology (OT) or Industrial Control System (ICS) is at the core of today’s automated production floors. Machines across age, usage, and location are now connected via IoT and OT and visible on a single interactive dashboard. As the benefits of industrial automation continue to grow and support manufacturers in reducing downtime, wastage, and increase efficiency, the web-based connectivity and remote management capabilities also create vulnerabilities for the plant.
Most manufacturers either overlook or simplify the idea of securing their OT. Due to the lack of education and awareness on specific security applications and best cybersecurity practices for OT, many factories try to adopt the same security measures utilised by IT. IT cybersecurity is built for an office environment with desktops, laptops, servers, and cloud storage with regular patches, anti-virus updates, and isolation of affected devices without much disruption to the workflow.
OT is a cyber-physical environment that involves machines, networks, remote management, and cloud deployments. Cybersecurity for this environment has to be more dynamic and controlled in its implementation as infiltration will cause safety risks, downtime, and financial losses to the manufacturer with potential for the whole ICS to be affected. In short, your production can come to a halt if your OT cybersecurity can’t detect, isolate and eradicate intrusions on the go.
Below is a quick summary of how IT differs from OT in terms of implementation and impact:
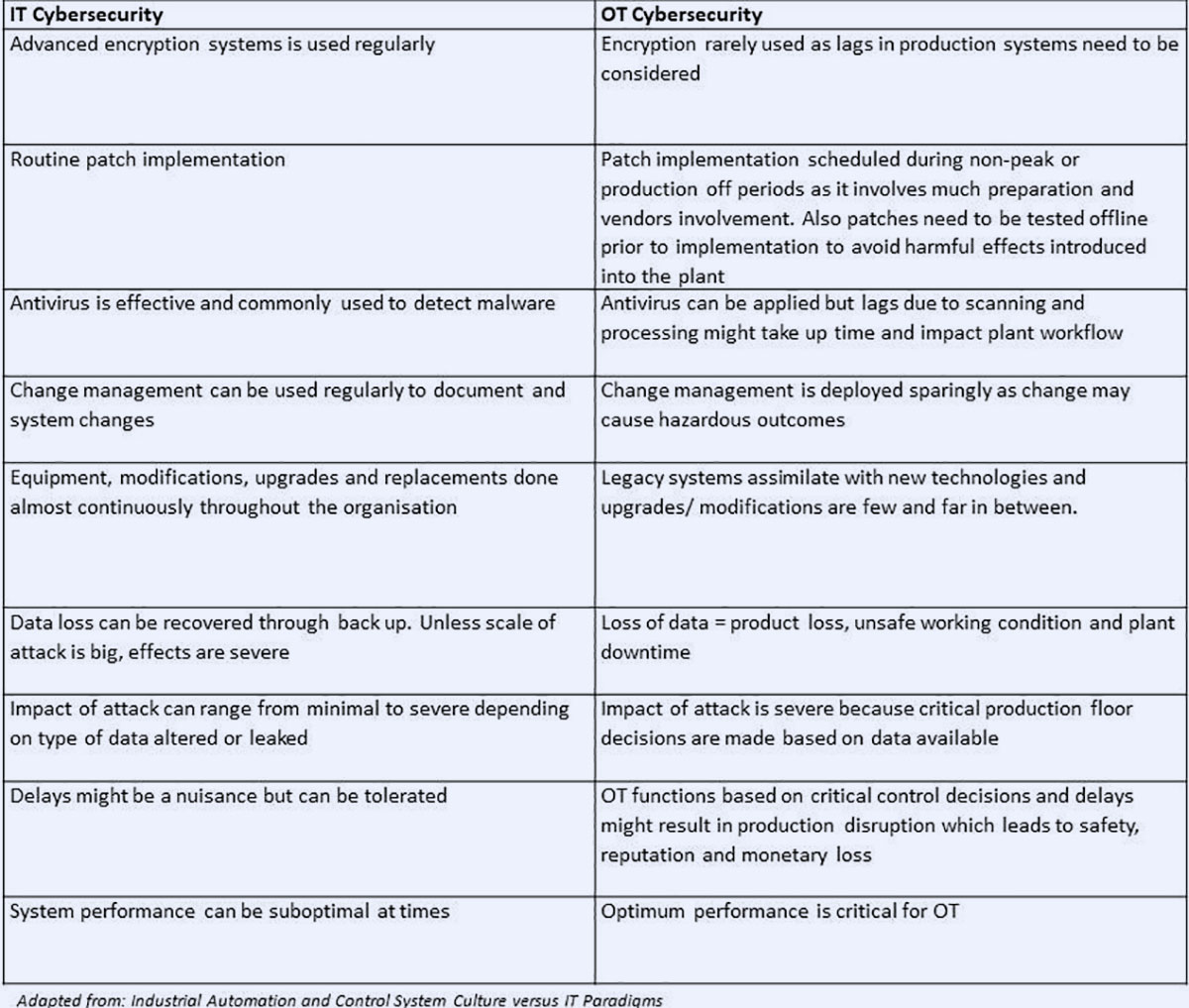
As such, manufacturers need to proactively look at securing their OT systems with customised cybersecurity solutions to protect their production network effectively. While integrity, confidentiality, and availability are key focus areas for OT cybersecurity, the biggest concern about any OT system being infiltrated is SAFETY of the people on the line. This should be all the motivation a manufacturer needs to deploy a customised OT cybersecurity solution.





